Install a JWT library
We use JSON Web Tokens to securely authenticate your users. First, install the appropriate JWT library for your server.Get SSO Private Key
Go to your Suggix Dashboard → Settings → Developer to find your SSO private key.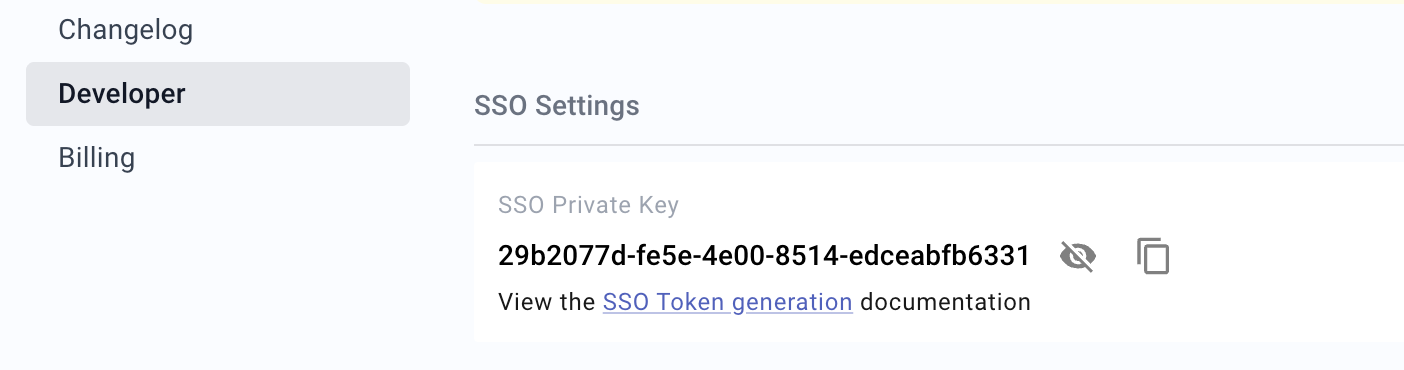

Store this key securely on your server and never share it publicly.
Install a JWT library
- Node.js
- C#
- Go
- Java
- PHP
- Python
- Ruby
Copy
npm install --save jsonwebtoken
Copy
dotnet add package System.IdentityModel.Tokens.Jwt
Copy
go get github.com/golang-jwt/jwt
Copy
# See instructions here:
https://mvnrepository.com/artifact/io.jsonwebtoken/jjwt
Copy
composer require firebase/php-jwt
Copy
pip install PyJWT
Copy
sudo gem install jwt
Generate the JWT Token
- Node.js
- C#
- Go
- Java
- PHP
- Python
- Ruby
Copy
var jwt = require('jsonwebtoken');
var PrivateKey = 'Your SSO Private Key';
function createSSOToken(user) {
var userData = {
email: user.email,
name: user.name,
id: user.id, // optional
photo_url: user.photo_url, // optional
};
return jwt.sign(userData, PrivateKey, {algorithm: 'HS256'});
}
Copy
using System;
using System.IdentityModel.Tokens.Jwt;
using System.Security.Claims;
using System.Text;
using Microsoft.IdentityModel.Tokens;
public class JwtHelper
{
private static string PrivateKey = "Your SSO Private Key";
public static string CreateToken(User user)
{
byte[] keyBytes = Encoding.UTF8.GetBytes(PrivateKey);
var securityKey = new SymmetricSecurityKey(keyBytes);
var credentials = new SigningCredentials(securityKey, "HS256");
var header = new JwtHeader(credentials);
var payload = new JwtPayload
{
{ "email": user.email },
{ "name": user.name },
{ "id": user.id }, // optional
{ "photo_url": user.photoURL }, // optional, but preferred
};
var securityToken = new JwtSecurityToken(header, payload);
var handler = new JwtSecurityTokenHandler();
return handler.WriteToken(securityToken);
}
}
Copy
import (
"github.com/golang-jwt/jwt"
)
const PrivateKey = "Your SSO Private Key"
func createSSOToken(user map[string]interface{}) (string, error) {
token := jwt.NewWithClaims(jwt.SigningMethodHS256, jwt.MapClaims{
"email": user["email"],
"name": user["name"],
"id": user["id"], // optional
"photo_url": user["photo_url"], // optional
})
return token.SignedString([]byte(PrivateKey));
}
Copy
import java.util.HashMap;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
public class SSOTokenCreator {
private static final String PrivateKey = "Your SSO Private Key";
public static String createToken(User user) throws Exception {
HashMap<String, Object> userData = new HashMap<String, Object>();
userData.put("email", user.email);
userData.put("name", user.name);
userData.put("id", user.id); // optional
userData.put("photo_url", user.photoURL); // optional
return Jwts.builder()
.setClaims(userData)
.signWith(SignatureAlgorithm.HS256, PrivateKey.getBytes("UTF-8"))
.compact();
}
}
Copy
use \Firebase\JWT\JWT;
const PrivateKey = 'Your SSO Private Key';
function createSSOToken($user) {
$userData = [
'email' => $user['email'],
'name' => $user['name'],
'id' => $user['id'],
'photo_url' => $user['photo_url'], // optional
];
return JWT::encode($userData, PrivateKey, 'HS256');
}
Copy
import jwt
private_key = 'Your SSO Private Key'
def create_sso_token(user):
user_data = {
'email': user.email,
'name': user.name,
'id': user.id, # optional
'photo_url': user.photo_url, # optional
}
return jwt.encode(user_data, private_key, algorithm='HS256')
Copy
require 'jwt'
PrivateKey = 'Your SSO Private Key'
def createSSOToken(user)
userData = {
email: user.email,
name: user.name,
id: user.id, #optional
photo_url: user.photo_url, # optional
}
JWT.encode(userData, PrivateKey, 'HS256')
end